Is there someplace to get this list of passwords? I’m not worried about my current passwords being on there, but there was one I used years ago that I still haven’t found on any list. I’m curious if it’s on there yet.
The list has been added to haveibeenpwned.com, you can check your passwords here.
OH NO, IT’S ON THERE!
…anyway…
I use https://monitor.mozilla.org
Edit. Oh, you mean the actual list.
Yeah there’s no question: your data is not safe. There are like 3-4 data breaches every day because no one holds these companies accountable for protecting your data.
Yeah there’s no question: your data is not safe.
Is that really a question when companies like Facebook, Google, Microsoft, your bank, etc. all claim your data as their property then sell it for profit, while offering no consideration in return?
Those companies don’t sell your data, they just USE it to sell all kinds of other shit.
Many do sell data, actually. I just literally made a post about this, with real figures instead of numbers I’ve previously pulled out my ass. If you click my profile it should be high up there (otherwise it will be difficult for me to find it in your own instance). This is my instance’s version of the post: https://lemm.ee/post/21285233
The main source stated that the “legal” data brokerage industry, that is companies who simply buy and sell user data, was worth $319 billion in 2021.[1]
The global data broker market was valued at US$319.030 billion in 2021 and is expected to grow at a CAGR of 7.96% over the forecast period to reach US$545.431 billion in 2028.
Data brokers are the companies that collect the information of users through the internet legally and further, provide this data to various companies
You are right though, some companies (eg Google) simply collect user data and use it for themselves, they don’t really sell much of what they have. This means that my figure where your average user is owed $40 per year would be an underestimation, possibly a very large one.
We could maybe add the value of Google to the industry value, however even then Google’s value is offset by their various loss-leading ventures - the true value of the data Google holds is completely obscured. In any case, I need to go to bed! XD
Of course they do. I said “these companies”. As in MS, Google and Facebook. They’re not sellers, they’re buyers.
Well, they do also sell data access to governments. The argument when the government requested data from them was “we aren’t set up for this, it will incur significant expenses, we’ll have to develop solutions then set up and staff a department to handle requests”, which the government paid for. It’s not directly purchasing the data, but it is effectively.
You got a source for that?
I’ll be honest, I’m still tired from last night lol, too much so to go digging. We’re also talking about something that has been the norm for more than a decade now - Google have long since established their processes for dealing with government requests. This may have started sometime around 2012, perhaps even earlier. I probably read it in an Ars Technica article, at a guess, but it could also have been something I stumbled upon on reddit.
Removed by mod
I have worked IT for 2 Fortune 500 companies and let me tell you NONE of them took data security seriously.
Neither has 90% of any of the other sites I’ve worked on.
In my experience so few companies bother spending appropriately on it because IT is considered a cost center instead of a needed service.
Use a password manager. Every account gets a different (and strong) password.
Obviously any reputable password manager is better than none at all, but I strongly recommend using KeepassXC on the desktop and a suitable mobile client for phones and tablets, and syncing the database across devices with an encrypted peer to peer sync tool like Synching.
I’ve always been nervous about being part of a large, juicy cloud hosted target, and LastPass was the proof that those concerns are well-founded.
KeepassDX for mobile is on F-Droid and can use the same file as accessed from KeepassXC from Laptop, synced by Syncthing.
I can also recommend Keepass2Android, which I’ve been using for years.
Yep. If you’ve got the technical knowledge and a server, self hosting Bitwarden is quite easy. And your vault is end to end encrypted.
Additionally, I use simplelogin so they also gotta match unique passwords with my unique emails and then get past 2fa.
All cool and dandy, until you have to type that random 50 letter string on your TV.
You don’t need to make it that long.
And also most TVs or whatever you’re streaming with has a way to type from your phone nowadays. Apple TV, Chromecast, Android TV, heck I think even Xbox.
It’s kinda nice on Apple TV your phone will suggest autofill passwords for the TV, even from theirs party password managers like Bitwarden.
Android tv’s arent that old. 10 years max. 5 years since it’s affordable for most people. Is it unreasonable to own a 5 year old non-smart tv? I think not. I think it’s weird that so many people assume everyone owns a smart tv.
In what scenario would you need to type in a password on a non-smart TV though? Parental lock?
You’re not wrong but in what context would you be putting in passwords on a non-smart device
Also it’s not just smart TVs. You can hook up streaming sticks and boxes and game consoles to anything with an HDMI port
Many PW managers let you generate passphrases, which are all around better than random strings. Length is the most important factor so
finance-caffeine-utopia-redress-unseen
Is way stronger and easier to remember (and type) than
Fl7$j4FWw)&5O
Huh, TIL. I had no idea that was an option but that’s super useful for things I need to type in on a device with no keyboard, or even things I can’t access my password manager for. Thanks for the protip there!
Is it really safer? I mean when trying to bruteforce a password, one would have to make a guess whether it’s a passphrase or not. But if you decided to check for pass phrases, wouldn’t the one you posted be cracked in 5 times the amount of words in that dictionary? I’m not sure how large the vocabularies of the generators are, but I would guess a random 17 char password might be safer than a 5 phrases password?
It’d be dictionary length to the fifth power, not times five.
but I would guess a random 17 char password might be safer than a 5 phrases password
And you would be very wrong about that. A 5 phrase password has entropy. “finance-caffeine-utopia-redress-unseen” is 28 characters. If you add in a different symbol between the words and add a number somewhere, this password becomes incredibly difficult to brute force.
I’ll let xkcd explain it better.
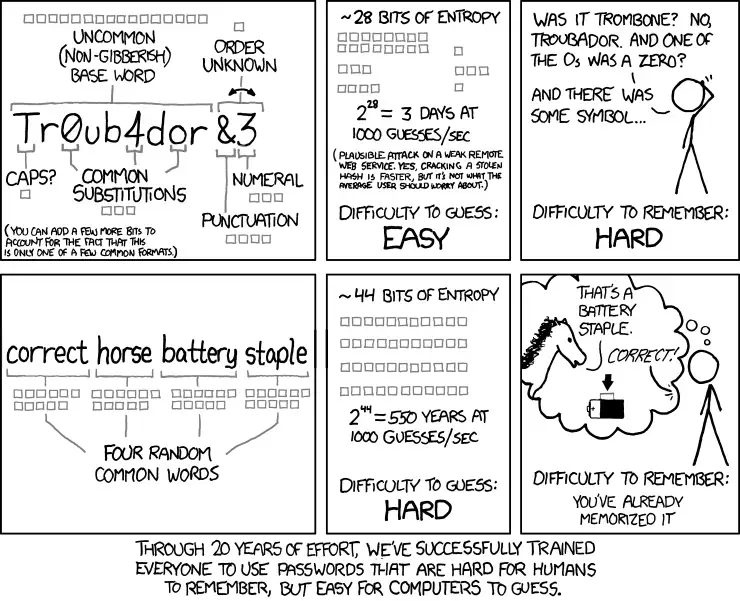
Youre right,different separators, numbers and even capital letters change my theory alot
And pass phrases are faster to type and with less typos even though they need more characters than passwords to be the same secure.
deleted by creator
For symmetric keys, since they cannot be weakened using quantum computing, their strength can be assessed by their bit-equivalent amount of entropy:
- 40 bit or less - easily breakable
- 64 bit - not so easy, but doable
- 128 bit or more - basically unbreakable
Those are equivalent to, respectively:
- 0-9 - 12, 19, 38 characters
- a-z - 9, 14, 28 characters
- a-z0-9 - 8, 12, 25 characters
- A-Za-z0-9 - 7, 11, 22 characters
- A-Za-z0-9+special - 7, 10, 21 characters
Moral of the story: drop the special characters, and even the numbers… and even the uppercase. A 30+ character long all-lowercase pass phrase, is already unbreakable.
Check @falsemirror@beehaw.org:
finance-caffeine-utopia-redress
-unseen…is already over 128 bits.
I had to do that recently, ended up being easier to just temporarily change the password to something short on a pc, then change it back after.
Cybersecurity is expensive and doesn’t contribute directly to profits. It can prevent serious damages (legal, financial, and reputation) but that requires long-term thinking. Most executives don’t look past quarterly earnings.
Neoliberals: “OK how about we keep doing the thing that makes them care only about next quarter, but give them a $1 fine every time they’re negligent?”
On the other end, prevent malicious actors from using identity theft to get credit cards and loans: freeze your credit.
- Transunion: https://www.transunion.com/credit-freeze
- Experian: https://www.experian.com/freeze/center.html
- Equifax: https://www.equifax.com/personal/credit-report-services/credit-freeze/
It’ll be a minor hassle when you go to get a car loan, and forget that your credit is frozen - but you will be able to temporarily unfreeze it from your phone.
Let me tell you something about Betteridge’s law for headlines
This story is a great demonstration of my maxim that any headline which ends in a question mark can be answered by the word “no.” The reason why journalists use that style of headline is that they know the story is probably bullshit, and don’t actually have the sources and facts to back it up, but still want to run it
Thank you so much for introducing me to this
My pleasure :)
id recommend custom email addresses… most places let you tack on arbitrary strings to your email address or if you have your own domain, you can just forward all and use anyname@yourdomain on the fly.
no single system compromise can affect any other system
But many sites don’t support that, unfortunately.
DHL for example will happily create an account for you with the “mail+xyz@gmail”, but will sometimes drop the suffix internally. You can’t reset your password for example. Super annoying.
Yeah I’ve come across several websites that don’t let you use anything other than the usual suspects (@gmail.com, @yahoo.com, @live.com, etc.) but MOST of them let you use whatever you want.
I’m actually gonna go a step further and recommend using email aliases.
Firefox Relay, AnonAddy, Proton, etc.
deleted by creator
yeah that will give you ‘reply’ ability, but ive noticed i almost never actually need that extra bit.
Well, it gives you privacy, because your accounts are not tied to your domain.
Additionally anyone who finds out you’re using a catch-all can spam you with 100 different email addresses and it’s like spam callers who call you from 100 different numbers, you can’t block them all.
I speak from experience.
i’ll give ya the domain leak…
but i have hundreds of addresses across a few domains, and ive had to setup reply for maybe 5.
i have no issues with spam, not sure why ya brought that up. most providers have pretty good filters these days
Someone caught onto my antics and started fucking with me and sending me all kinds of creepy emails. Ended up having to kill the catch-all, along with changing all the emails registered to it.
Any lemmy instances included in this breach?
Edit: Doesn’t appear to be the case. At least, when I checked mine they were fine.