

Why not Actual Budget, which is also self-hosted, open-source bucket budgeting based off YNAB, however it appears to be a lot more mature.
They also transparently run the project on Open Collective which I like: https://opencollective.com/actual


Why not Actual Budget, which is also self-hosted, open-source bucket budgeting based off YNAB, however it appears to be a lot more mature.
They also transparently run the project on Open Collective which I like: https://opencollective.com/actual


Very true. The discussion helped me, as I did think it meant not easily editable.
As root of course you can change the system to be any other type of system (layer packages, rebase, whatever), but I did assume it meant not easily modifiable in it’s current state.


My comment in the comment chain was:
An attacker escaping from a container can’t be system root as Podman runs rootless (without some other exploit or weak password).
We could give the op the benefit of the doubt and thinking that they were saying that the attacker inside the container managed to gain root inside the container.


While you are correct, any system is compromised if you have root, so isn’t that irrelevant at that point?


Makes sense. An “immutable” distro provides no additional security benefit, however CoreOS does have a reduced attack surface area compared to other distros, which itself is a benefit.


edit: “Immutable” means “all of them are the same”, not “unchangeable”.
You sound confident, but the fact that Fedora is using the term “immutable” makes me wonder if you actually have domain expertise here.
Immutable means immutable. It would be strange for them to call it that if it actually means “completely irrelevant from a security perspective”.
Unless you provide some evidence to the contrary I’m going to assume you aren’t correct.


They 100% can.
An attacker escaping from a container can’t be system root as Podman runs rootless (without some other exploit or weak password).
The filesystem itself is also read-only.
/dev/nvme0n1p4 on /sysroot type xfs (ro)
/dev/nvme0n1p4 on /usr type xfs (ro)
/dev/nvme0n1p3 on /boot type ext4 (ro)


Selfhosted Gitea is a way to get a wiki, bug tracker or whatnot - collaborate, for example, but it’s not necessary to have a Git server for your personal use.
No, but it is amazing for browsing your repos and visually seeing what you did in a past commit or a branch, while your IDE is open to your latest code. Or copying and pasting something that you need from a different repo.
For Git experts, sure they can probably do all that better inside their IDE or CLI, but for us plebs, having your own Forgejo is incredible 😍
I have mine configured to disable the wiki and issues, etc, it’s just the repo browser.


I use UCore for my homelab and it’s been flawless. Absolutely no issues. I run around 50 containers, LLMs, and host some public sites with Caddy.
The major thing that’s keeping me away from CoreOS/ uCore is all the ignition-butane-stuff. From what I’ve heard, it’s needlessly complicated
It’s super super easy. Run a docker one-liner on your existing local server or laptop to host a quick webserver:
docker run -p 5080:80 --name quick-webserver -v "$PWD":/var/www/html php:7.2-apache
And put this Ignition file in the directory from above: https://github.com/ublue-os/ucore/blob/main/examples/ucore-autorebase.butane
That’s it, that’s the only steps. Boot off the ISO and type in the hosting URL from above.
You’ll only need that when building the server the first time.


Thank you for posting this - I have had a play and it’s excellent.
I am a newbie in the Linux world and have been looking for something to replace the excellent WinSCP. XPipe is the first application I’ve used on Linux that actually makes remote SSH/SCP browsing easy to do, while still being able to handle more complicated SSH auth than just user/pass.


Not the FIPS one, I use the normal 5 series.
Yubikeys are great because you can also add your TOTP codes on there, but require a physical touch to generate the codes.
You can do that with other products like the NitroKey as well, but the implementation is not as good - example the secrets are not encrypted on the NitroKey.


I assumed that yubikeys would be found pretty much only in enterprise environments but perhaps I was wrong there.
As a datapoint, I am a home user and use Yubikeys. For example, they are one of the 2FA options supported by Bitwarden for home users.
I have recently trialed both NitroKey and OnlyKey to see if I’d want to replace my Yubikey with either of those, but the Yubikey is sadly superior. (Sadly because it’s not as open as those other two options.)


stores my notes metadata in proprietary database format?
Obsidian note metadata is stored in YAML in the markdown note file itself. That’s about as non-proprietary as it gets.
Not sure why you hate Obsidian. I don’t love it and would switch to a FOSS alternative if there was something comparable, but at least I’m not making crap up about it.


It makes for very handy use cases where other applications can work on the same data. This could be easily adding content into your notes (without needing an API to do so), using external editors for working on certain aspects of your notes, or even just the super handy convenience of having everything in one directory structure.
My Obsidian notes are right inside the same folders as the PDFs and other resources they refer to. I don’t have to have a tree structure inside my notes and then the same tree structure in my hard drive or Dropbox or wherever with all my other files.
I was a 10+ year Evernote veteran, and I couldn’t go back to the single DB style like Evernote or Trillium. I wish there was an open source competitor to Obsidian, but alas not yet.
And as @acockworkorange@mander.xyz rightly points out, people (me!) have been burned in the past by a program becoming obsolete and having your files stuck in some proprietary format. Plain files right in a folder on the disk is the way to go.


I mean in your linked thread it says:
I have some 15K notes in Obsidian and it runs fine.
I personally have 4000+ notes in Obsidian and it runs fine 🤷
Here’s also Obsidian with 100,000 notes and it performs fine. This test is also 2 years out of date.
They might be talking about posts like this (which I would love to have refuted, as this kind of info has so far kept me from using Docker significantly):
Containers are isolated from the host by default.
Are you certain about that? My understanding is that Docker containers are literally just processes running on the host (ideally rootless), but with no isolation in the way that VMs are isolated from the host.
If you have some links for further reading it would be great, as I have been extremely cautious with my Docker usage so far.
I haven’t found anything to refute this, but this post from 2017 states:
In 2017 alone, 434 linux kernel exploits were found, and as you have seen in this post, kernel exploits can be devastating for containerized environments. This is because containers share the same kernel as the host, thus trusting the built-in protection mechanisms alone isn’t sufficient.
If someone exploits a kernel bug inside a container, they exploited it on the host OS. If this exploit allows for code execution, it will be executed on the host OS, not inside the container.
If this exploit allows for arbitrary memory access, the attacker can change or read any data for any other container.


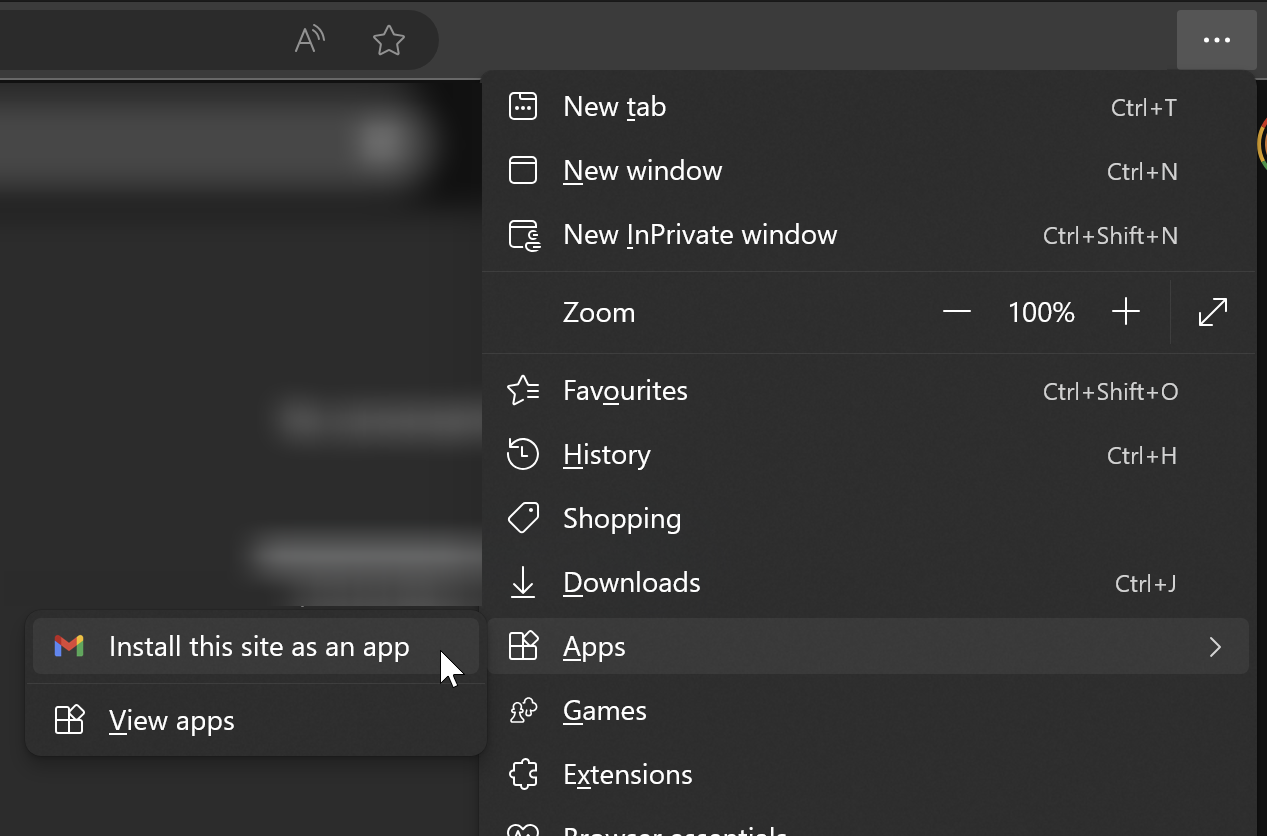
In Edge (and maybe Chrome?), open the menu for any website, then go to Apps > Install this site as an app.
Boom, webpage as standalone program. They appear on your start menu and you can pin them to your taskbar. I do this with all my frequently used tools and it makes things much faster to arrange them all on a screen or get back to them.
Bonus tip: You can use Win+1, Win+2, Win+3, etc to instantly switch to that pinned app on your taskbar.
It’s like YNAB4. For those of us in that vintage it’s perfect. If you’re using the newer YNAB it might have missing features.